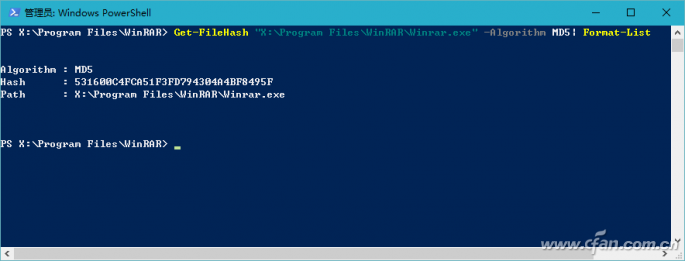
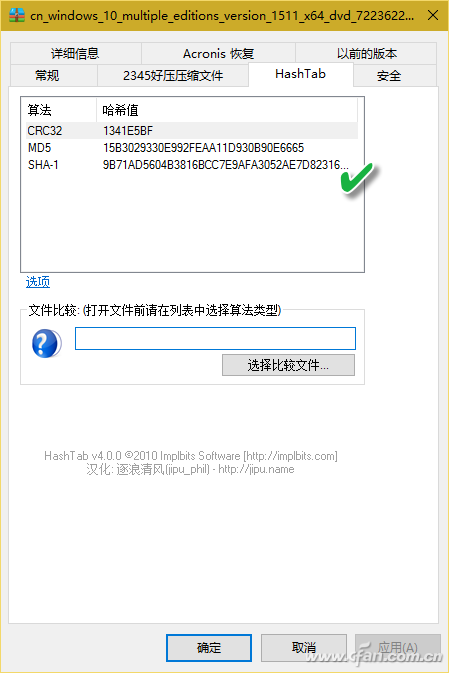
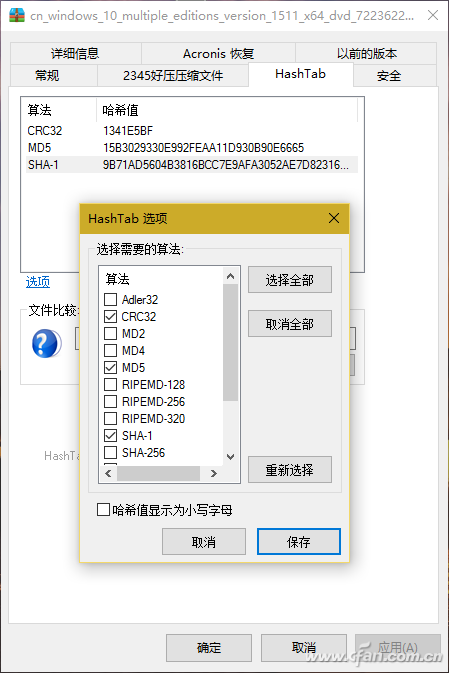
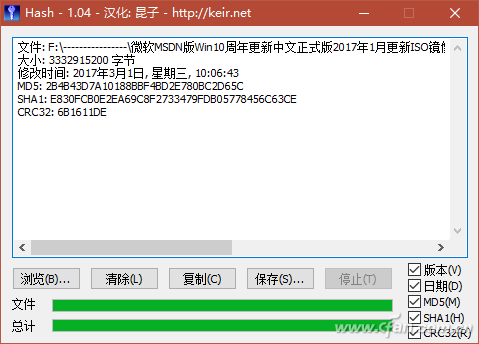
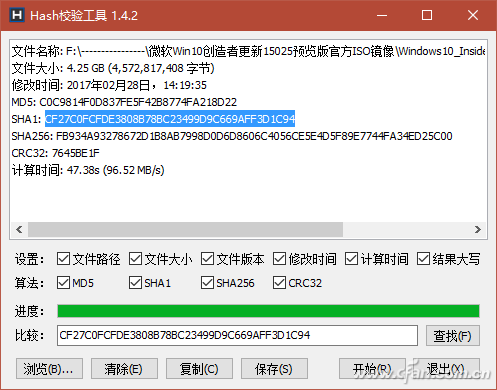
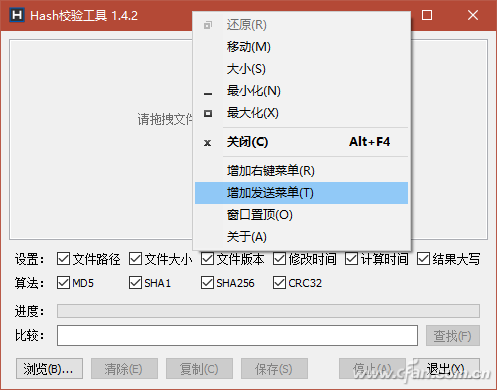
Have you ever noticed that while download tools like Thunder can automatically verify downloaded data, some software download pages—such as those for Windows installation packages—also provide checksums like MD5, SHA1, and CRC32? So, what other types of verification data are available, and how can an average user make use of them? File verification is the process of checking whether a file on a website matches the one you've downloaded. This is usually done using checksums such as MD5, SHA1, or CRC32. These codes are strings generated by a program based on the file's content. If the file remains unchanged, the checksum will always be the same. However, if the file is altered or corrupted during download, the checksum will change. For example, Microsoft provides checksums for its Windows 10 ISO files. If you're unsure whether a third-party site offers the original ISO, you can compare the checksums of the downloaded file with the ones provided by Microsoft. A match means the file is genuine. Right-click Property View If you frequently need to verify files, consider installing HashTab 4.0 for Windows. After installation, it adds a "HashTab" section to the file properties window. Right-clicking a file and selecting "Properties" will show the hash values being calculated (Figure 1). Depending on the file size, it may take a few seconds to compute and display the results (Figure 2), including MD5, SHA1, and CRC32 values. Although the default algorithms shown are limited, HashTab supports over a dozen more. By right-clicking the hash list and choosing "Options," you can select additional algorithms (Figure 3). Tip: You can generate a checksum before uploading a file online and paste it for others to verify. Similarly, after downloading, you can use this method to check against the official checksums to ensure the file hasn't been tampered with. Drag-and-Drop Method If you don’t often verify files, there’s no need to install plugins. Instead, use a lightweight tool like Hash_V1.04. Simply drag and drop the file into the software window, and it will automatically calculate MD5, SHA1, and CRC32 checksums (Figure 4). You can then copy or save the result easily. Another useful tool is the Hash Verification Tool V1.4.2, which also generates SHA256 hashes in addition to the common ones. It allows you to verify multiple files at once and even search for specific hash values, making it ideal for large-scale checks (Figure 5). Tip: This tool also includes options like adding a right-click menu, sending to a folder, and keeping the window on top, improving usability (Figure 6). Using PowerShell for Verification In Windows 10, you can also verify files using PowerShell. The command Extended Reading: Dealing with 'Man-in-the-Middle' Attacks While checksums help ensure file integrity, they are not foolproof. Attackers can modify files and provide fake checksums, tricking users. To prevent this, MAC (Message Authentication Code) was introduced. Unlike simple checksums, MAC requires both the sender and receiver to agree on a shared secret key. Even if a third party intercepts the file, they cannot generate the correct MAC without the key. This ensures the file's authenticity and protects against tampering.
XB4 series Pushbutton Switch are used in industrial for controlling circuits of AC50Hz or 60Hz,rated operation voltage 380V or below and DC operational Voltage 220V or below for controlling in magnetic starter, contactor,relay and other electrical circuits. The buttons indicators can also be used in the place with indicated light or signal. They meet with the standards: IEC 60947-5-1.
XB4 Series Metal Pushbutton Switch is the new design in the field of Push Button Switch. Which with stronger metal plate and very easy to be installed.
XB4 Series Pushbtton Switch,Push Button Power Switch,Mini Push Button Switch,Push Button Lamp Switch Ningbo Bond Industrial Electric Co., Ltd. , https://www.bondelectro.com
Get-FileHash File Path | Format-List gives the SHA256 hash by default. To get other hashes like SHA1 or MD5, replace "SHA256" with the desired algorithm (Figure 7). Note that spaces in file paths must be enclosed in quotes, and PowerShell does not support CRC32.