Utility Scale Energy Storage,Solar Energy System,Solar Photovoltaic Panels,Photovoltaic Pv Systems EMoreShare International Trade (Suzhou) Co., Ltd , https://www.emoreshare.com
Learn about the latest white papers in the LoRa Alliance and 31 questions and answers on LoRa
LoRa is one of the key technologies in the LPWAN (Low-Power Wide-Area Network) domain. It is a long-range wireless communication solution based on spread spectrum technology, developed and promoted by Semtech. LoRa has revolutionized the traditional trade-off between transmission distance and power consumption, offering users a system that enables long-distance communication, extended battery life, and high capacity, thereby expanding the reach of sensor networks. Currently, LoRa operates in unlicensed global frequency bands such as 433 MHz, 868 MHz, and 915 MHz.
Before diving deeper into LoRa, let's start with the latest white paper from the LoRa Alliance, which provides insights into the security aspects of LoRaWAN and addresses 31 common questions about LoRa technology.

The latest white paper from the LoRa Alliance focuses on providing complete end-to-end encryption for IoT application vendors. Security is fundamental to all applications, and the LoRaWAN protocol was designed with security in mind from the beginning. However, security involves multiple layers, especially when it comes to the encryption mechanism used in LoRaWAN.
This white paper explains the security features of the current LoRaWAN protocol, starting with an overview of its security attributes and then delving into specific implementation details. Finally, it outlines various security design approaches within LoRaWAN.
### LoRaWAN Security Properties
The security design of LoRaWAN aligns with its core principles: low power consumption, low complexity, low cost, and scalability. Since devices are often deployed in the field and operate for several years, security must be comprehensive and forward-looking. LoRaWAN follows advanced security principles, including the use of standardized algorithms, thorough algorithm reviews, and end-to-end security mechanisms.
Key security features include two-way authentication, integrity checking, and privacy mechanisms. Two-way authentication ensures that only legitimate and authorized devices can connect to the network. MAC and application messages in LoRaWAN are inherently authenticated, protected for integrity, and encrypted, ensuring that traffic remains unchanged and originates from a legitimate device.
LoRaWAN also supports end-to-end encryption between the terminal device and the server, making it one of the few IoT networking technologies to offer this level of security. In contrast, traditional cellular networks typically encrypt data at the air interface but transmit it as plain text in the carrier’s core network.
To address this, users must implement additional security layers, such as VPNs or TLS, which may not be ideal for LPWAN due to increased power, complexity, and cost. LoRaWAN avoids these issues by integrating encryption directly into the protocol.
The security mechanisms rely on well-tested and standardized AES encryption algorithms, which have been extensively studied and recognized by NIST as highly secure. LoRaWAN uses AES-CMAC for integrity protection and CTR for encryption. Each LoRaWAN device is assigned a unique 128-bit AES key (AppKey) and another identifier (DevEUI), both used in the device identification process.
The assignment of EUI-64 identifiers requires obtaining an OUI from the IEEE, while the LoRaWAN network uses a globally unique 24-bit identifier assigned by the LoRa Alliance.
### Secure Application Load
End-to-end encryption of application data occurs between the terminal and the server. Integrity protection is achieved through frequency hopping, with secure transmission schemes like HTTPS and VPNS used between the network and the server.
Two-way authentication ensures that both the terminal and the network possess the AppKey. This is demonstrated during the join request process, where AES-CMAC (using the AppKey) is loaded into the device and backend receiver.
After mutual authentication, two session keys are used: one for protecting and encrypting the LoRaWAN MAC command and application load (NwkSKey), and another for encrypting the end-to-end application load (AppSKey). NwkSKey is stored on the network to verify packet authenticity, while AppKey and AppSKey are hidden to prevent application load decryption.
Data integrity and privacy are ensured through two session keys. Each payload is encrypted using AES-CTR and includes a frame counter, message integrity code (MIC), and AES-CMAC to prevent tampering.
### Physical Security and Cryptography
The physical security of LoRaWAN devices is critical, as AppKeys and derived session keys are stored in the device. If a device is physically compromised, these keys are stored in tamper-resistant memory and difficult to extract.
Cryptography in LoRaWAN uses AES in CTR mode, which leverages XOR operations. This reinforces the AES algorithm by assigning a unique AES key to each block cipher.
Session key distribution relies on the AppKey, which allows operators to derive AppSKey and decode the network if they gain access. To prevent this, the server manages the AppKey, and key derivation is handled by entities other than the operator. The upcoming LoRaWAN 1.1 protocol will introduce two master keys: one for the network (NwkKey) and one for the application (AppKey).
Backend interfaces are secured using HTTPS and VPNS to protect communication between the network and the application server. Implementation and deployment security depend on cooperation across all parties, including manufacturers, suppliers, and operators.
### Definitions and Additional Notes
- **AES**: Advanced Encryption Standard – a symmetric key-based encryption algorithm used for message encryption and identity authentication.
- **CMAC**: Cipher-based Message Authentication Code.
- **CTR**: Counter Mode Encryption Standard – a mode of operation for AES.
- **AES-CMAC**: Message authentication code using AES for integrity and authenticity.
- **CBC**: Cipher Block Chaining – a mode of operation for AES.

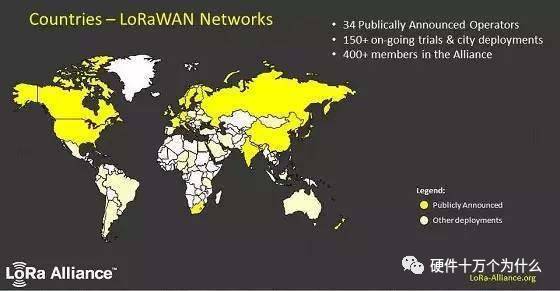
The final image shows the global deployment map of the LoRa Alliance, highlighting its extensive network of over 400 members, more than 150 ongoing deployments worldwide, and 34 operators.
### 31 Questions and Answers About LoRa
1. **What is LoRa modulation?**
LoRa is a modulation technique that offers longer communication distances compared to similar technologies. It uses spread spectrum technology, specifically a variant called Linear Modulation Spread Spectrum (CSS) with Forward Error Correction (FEC).
2. **What is LoRaWAN?**
LoRaWAN is a MAC protocol for large-scale, long-range, low-power star networks, standardized by the LoRa Alliance.
3. **What is a LoRa Gateway?**
A LoRa Gateway is a multi-channel, multi-modulation device that relays messages between terminal devices and the central network server.
4. **What is the data rate of LoRaWAN?**
LoRaWAN data rates range from 0.3 kbps to 11 kbps, depending on region and configuration.
5. **How does LoRa differ from SIGFOX and NWave?**
LoRa uses spread spectrum technology, while SIGFOX uses narrowband BPSK, and NWave uses a Weightless standard similar to SIGFOX.
6. **What is a LoRa concentrator?**
A LoRa concentrator is equivalent to a gateway in the LoRa system.
7. **How does LoRa handle interference?**
LoRa modems can suppress co-channel GMSK interference by up to 19.5 dB, allowing reliable communication even in noisy environments.
8. **What is the data rate of LoRa?**
LoRaWAN defines specific data rates, but the actual rate depends on the chip and configuration.
9. **What is a LoRa endpoint?**
A LoRa endpoint is a device that communicates with the gateway using the LoRaWAN protocol.
10. **What is Adaptive Data Rate (ADR)?**
ADR adjusts the data rate to optimize performance, reliability, and network capacity.
11. **What is the maximum output power of a LoRa device?**
The chip pin output is +20dBm, but after filtering, it is typically around +19dBm.
12. **What is the cost of a LoRa solution?**
LoRa devices are relatively low-cost, with a typical bill of materials ranging from $2 to $5 per endpoint.
13. **How does LoRa Channel Activity Detection (CAD) work?**
CAD detects the presence of a LoRa signal without relying on RSSI, distinguishing noise from actual signals.
14. **Why might my LoRa device output less than 20dBm?**
Output power can be affected by RF components, software configuration, and PCB layout.
15. **Can I switch between FSK and LoRa modulation?**
Yes, switching between FSK and LoRa is possible via SPI register writes.
16. **How do I fix low output power issues?**
Check the correct pin (PA_Boost), software configuration, and PCB design for optimal performance.
17. **How is mass production testing done for LoRa devices?**
Key parameters like frequency tolerance, output power, and sensitivity are tested using a spectrum analyzer and FSK mode for sensitivity checks.
18. **How do I choose the right crystal for my LoRa device?**
For most designs, a ±10 ppm crystal is sufficient, but TCXO is recommended for lower bandwidths.
19. **How do I measure frequency accuracy in LoRa mode?**
Use the FSTX mode to generate a CW tone based on LoRa configuration settings.
20. **What is the relationship between BW, Rs, and DR?**
Theoretical formulas exist, but using the LoRa modem calculator is recommended for accurate evaluation.
21. **How do I choose BW, SF, and CR for LoRa?**
LoRaWAN typically uses 125 kHz BW, but other configurations are possible. Trade-offs between battery life, distance, and data rate should be considered.
22. **How to resolve communication issues between SX127x modules from different manufacturers?**
Check frequency offset, software settings, and ensure consistency in configuration.
23. **Why might a CRC-enabled LoRa packet be received incorrectly?**
Incorrect header information can lead to false detection and packet errors.
24. **Can LoRa send or receive unlimited-length packets?**
No, the maximum packet length in LoRa mode is 256 bytes.
25. **How do I use DIOx pins in LoRa mode?**
DIO pins provide interrupt and status information, helping reduce MCU resource usage.
26. **Why are there two RSSI registers in LoRa mode?**
RegPktRssiValue measures the packet RSSI, while RegRssiValue is similar to FSK RSSI.
27. **How to calculate the bit rate and transmission time of LoRa?**
Use the LoRa calculator provided by Semtech for accurate results.
28. **Can LoRa support 256-byte payloads at any data rate?**
Yes, but longer transmission times may affect performance in high-interference environments.
29. **Is LoRa a mesh, peer-to-peer, or star network?**
LoRa itself is a PHY and can support multiple topologies, but LoRaWAN uses a star architecture for optimal performance.
30. **Can LoRa support IPv6 and 6LoWPAN?**
Yes, LoRa is compatible with IPv6 and 6LoWPAN, with implementations by partners like Actility.
31. **What is the capacity of a LoRa Gateway?**
An SX1301 gateway can handle approximately 62,500 end devices if each sends a packet every hour.
As the LoRa Alliance and NB-IoT Alliance compete for market share, their differing technical characteristics and use cases make it challenging to meet all customer needs in one solution. Xiecheng Smart offers a comprehensive LoRa solution, including modules, base stations, and management platforms, and is a member of CLAA and the China NB-IoT Industry Alliance.