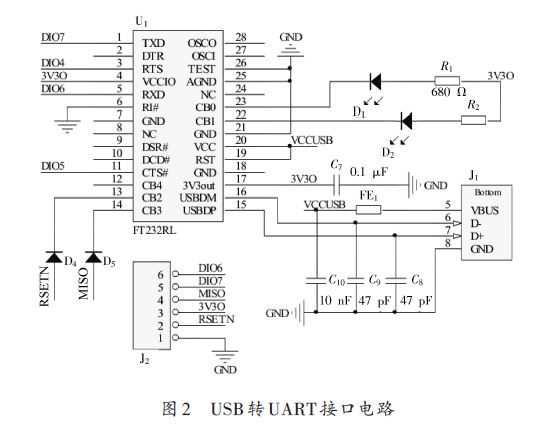
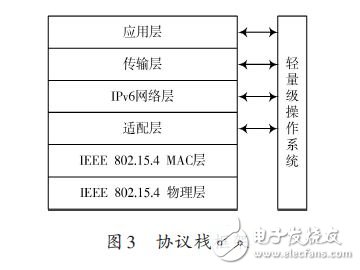
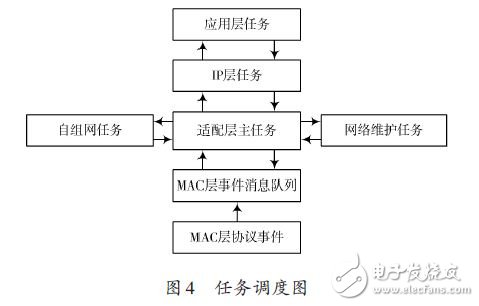
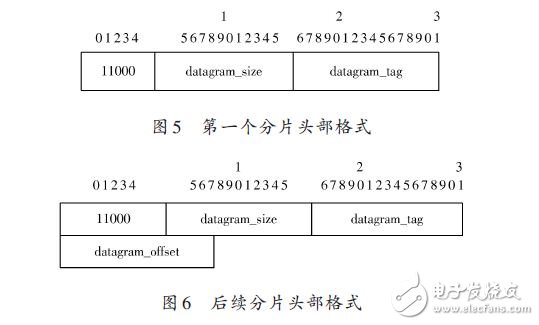
In this paper, the wireless sensor network is interconnected with IPv6 network. Based on the analysis of the existing insufficient access methods, a design scheme of wireless sensor network border router based on IPv6 is proposed. The scheme mainly describes the hardware and software design of the border router, and focuses on the design of the adaptive layer of the wireless sensor network protocol stack based on IPv6. Through the packet fragmentation and reassembly mechanism and the header compression mechanism, the protocol stack adaptation layer implements the transmission of IPv6 data packets in the IEEE 802.15.4 link. The experimental results show that the design scheme realizes the seamless integration of wireless sensor network and IPv6 network, and the data transmission is stable and reliable, and has practical application value. 0 Preface Wireless Sensor Network (WSN) has developed rapidly in recent years and has broad application prospects in the fields of environmental protection, industrial equipment monitoring, medical monitoring, farmland monitoring, smart home, municipal traffic management, and military reconnaissance. Many applications of wireless sensor networks require remote users to easily access, control, and use wireless sensor network resources. The wide application of TCP/IP has made it a de facto protocol standard. In addition, many excellent features of IPv6 make the interconnection and integration of wireless sensor networks and IPv6 networks the most realistic choice. At present, wireless sensor networks and IPv6 network interconnection mainly have two ways: gateway access and direct access. Among them, gateway access refers to the use of a gateway to perform protocol conversion between a wireless sensor network and an IP network to implement data forwarding tasks. However, gateway access also has many problems such as complex network structure and high cost; the direct access method is It means that the wireless sensor network node runs the IPv6 protocol directly, which enables seamless integration of the wireless sensor network and the Internet network. Wireless sensor networks are low-rate, low-power resource-constrained networks that are not suitable for direct operation of standard IPv6 protocols on wireless sensor nodes. This paper proposes a design scheme of wireless sensor network border router based on JN5148 module. This scheme can realize the seamless integration of wireless sensor network and IPv6 network, and proves the feasibility of the scheme through actual tests. 1 border router hardware design The border router hardware includes components such as a radio frequency module, a processor module, and a power module. The radio frequency module is responsible for receiving and transmitting IEEE 802.15.4 data frames; the processor module is responsible for parsing the received data frames, and selecting the path for forwarding processing; the power module is responsible for supplying power to other modules. The hardware structure of the border router is shown in Figure 1. 1.1 RF Module At present, there are many protocol stacks for different applications in the field of wireless sensor networks. Most of the protocol stacks use IEEE 802.15.4 as the wireless communication standard of the physical layer and the data link layer. The RF modules supporting IEEE 802.15.4 mainly include JN5148, Ember250, MC13192 from Jennic, CC2430 from TI, and XBEE modules from Digi. Among them, the JN5148 module integrates the RF chip and the processor, and has built-in IEEE 802.15.4 protocol. It does not need to design the radio frequency antenna interface by itself, and the development cost is low. In this design, Jennic JN5148 module is selected as the processor of the border router. And RF modules. The JN5148 module integrates a 32-bit RISC processor based on the OpenRISC core. It has a wireless transceiver fully compatible with the 2.4 GHz IEEE 802.15.4 standard, 128 KB of RAM running applications, and 512 KB of FLASH for storage applications. Most of the demand. 1.2 Serial Communication Interface Design Wireless sensor networks have small data traffic and low network bandwidth requirements. Therefore, a UART serial bus connection can be used between the border router and the Internet network. At present, the USB interface is commonly used in various network devices, and the conversion interface can be used to convert the USB interface into a UART serial bus interface. This paper selects the FTDI232R chip to complete level matching and interface conversion, and the FTDI232R is a programmable USB interface to UART. The integrated chip of the interface has a 3.3 V voltage output and is programmable to display data transmission and reception status. The specific circuit is shown in Figure 2. 2 Border Router Software Design 2.1 Protocol stack framework design The wireless sensor network protocol stack is the core of wireless sensor network software design, and is the basis of wireless sensor network networking, node and border routers, and data communication between nodes and nodes. In order to meet the all-IP interconnection of wireless sensor networks, it is necessary to streamline the IPv6 protocol and realize the transmission of IPv6 data frames in IEEE 802.15.4 frames. The border router designed in this paper uses an IPv6-based wireless sensor network protocol stack. The protocol stack framework is shown in Figure 3. The IEEE 802.15.4 physical layer is responsible for enabling and disabling RF transceivers, energy detection and channel scanning, clearing channel estimation, and modulation and demodulation of radio wave signals. The IEEE 802.15.4 MAC layer mainly performs channel access, link connection and disconnection, and error and flow control of data communication. The lightweight operating system ConTIki is responsible for scheduling and managing the various layers of the protocol stack to ensure the real-time performance of the protocol stack. The tasks included in the protocol stack include self-organizing network tasks, adaptation layer main tasks, network maintenance tasks, IP layer tasks, and application layer tasks. The task scheduling relationship is shown in Figure 4. The JN5148 module selected in this design integrates the physical layer and MAC layer protocol of IEEE802.15.4. Therefore, the focus of the protocol stack design is the adaptation layer, IP network layer and transport layer. 2.2 Adaptation layer design The establishment of the network is a basic task that the border router adaptation layer needs to complete. After the system is started, the ad hoc network task is responsible for establishing the network after the selected channel and the network 16-bit PAN_ID. The network maintenance task maintains the link between the parent node and the child node after the network is established, and reports the link and attempts to repair the link when the link is abnormal. The IEEE 802.15.4 physical layer data unit has a maximum of 127 B. The IPv6 requires a minimum MTU (MTU) length of 1 280 B. This length MTU is obviously not supported. The adaptation layer is IEEE 802.15. 4 Between the MAC layer and the IP layer, the main task of the adaptation layer is mainly responsible for managing the MAC layer protocol events, mainly completing the automatic address configuration of the node, the fragmentation and reassembly of the IP data packet, and the compression and decompression of the IP packet header. Implement the transmission of IP packets in an IEEE 802.15.4 link. 2.2.1 Address Mapping Mechanism Each node in an IPv6-based wireless sensor network needs to be configured with a unique IPv6 address, but manual configuration is cumbersome and it is difficult to guarantee address uniqueness. The wireless sensor network border router designed in this paper adopts a stateless address autoconfiguration mechanism. An IPv6 address consists of a global address prefix and an interface ID (IID). Because each RF module is assigned a globally unique IEEE EUI-64 identifier, a 64-bit MAC address, an EIPv-64 identifier can be used to obtain an IPv6 address interface identification ID for stateless address autoconfiguration. 2.2.2 Adaptation layer fragmentation and reorganization mechanism In order to reduce the overhead of the adaptation layer header, the adaptation layer header is divided into two formats: no fragmentation and fragmentation, which are used for packets with IP packet length less than MAC layer MTU and IP packet length greater than MAC layer MTU. Text. The adaptation layer non-fragmented frame header format is the same as the regular frame header, and the fragmentation frame header is further divided into the first fragment and the subsequent slice format, as shown in FIG. 5 and FIG. 6. When receiving the adaptation layer data packet, the node adaptation layer first checks whether the data packet is fragmented. If it is a fragmented data packet, after all the data fragments are reassembled into a complete IP data packet, the data is transmitted. Processing to the IP network layer; if a fragment is lost, discard all subsequent fragments of the IP packet. For the data packet sent by the IP layer, the node adaptation layer determines whether the IP packet length exceeds the link layer MTU length. If the link layer MTU length is exceeded, the IP data packet is fragmented and sent; if the link is not exceeded The layer MTU length is sent in a non-fragment format. Each data frame of the adaptation layer has a scheduling coded bit field (8 bits), and different scheduling coded bit fields represent different parsing modes, including non-fragmentation, fragmentation, IP header compression, UDP header compression, and pre-processing. There are many types of functions such as retention. The 11000xxx indicates that the data frame is the first fragment of the fragmented adaptation layer data frame, and the 11100xxx indicates that the data frame is the subsequent fragment of the fragmented adaptation layer data frame. Datagram_size: 11 b, indicating the total length of IP packets before the link layer is unpacked. The value of this field of all link layer fragments of the IP packet should be the same. Datagram_tag: 16 b, fragment ID, used to distinguish different IP packets of the same data source node. All link layer fragments of the same IP packet have the same fragmentation identifier, and the data source node updates (plus 1) the value of this field every time a complete IP packet is successfully sent. Datagram_offset: 8 b, the fragment offset, indicating the offset (in 8 B) of the fragment in all fragments. This field appears only in the second and subsequent fragments.
Home Humidifier Home Humidifier,Aroma Humidifier,Aromatherapy Humidifier,Personal Humidifier Shenzhen Dituo Electronic Co.,Ltd. , https://www.sz-dituo.com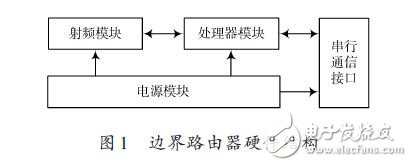
DITUO Home Humidifier Features as following: