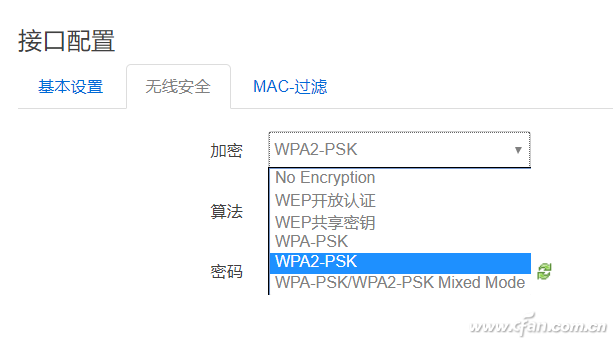
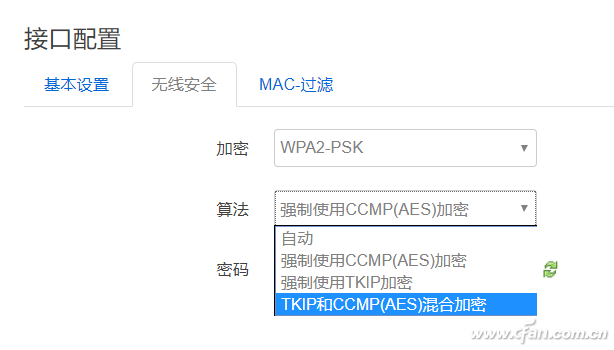
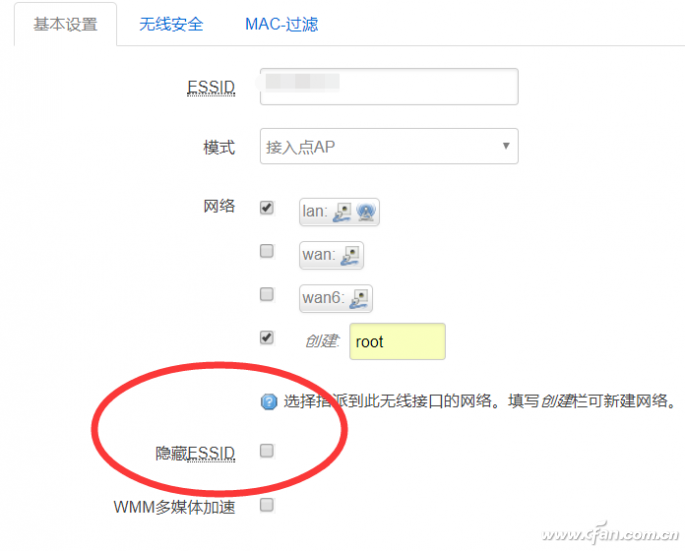
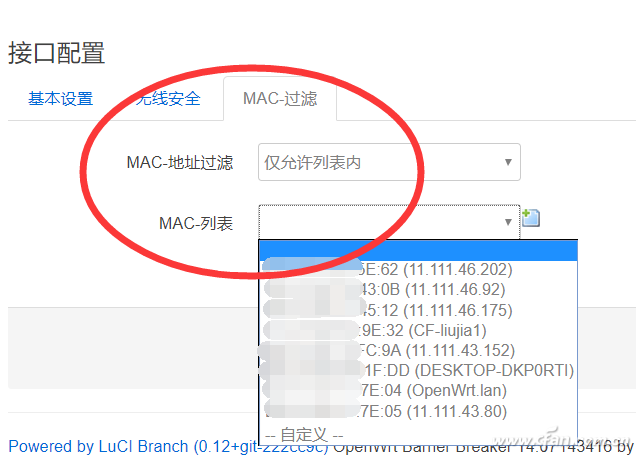
There was news in the morning news fan Fan that invented 13 years of WPA wireless encryption protocol has been cracked, attackers read wireless communication protocols between networked devices and wireless access points, and even can Modified to embed malware into the site. MacOS, Windows, iOS, Android, and Linux cannot escape this vulnerability. Many small partners have left a message asking what effect this will have, what WPA is again, and Xiao Bian will popularize it for everyone today. WPA is what? The full name of WPA is Wi-Fi Protected Access (Wi-Fi Network Security Access Protocol). It has WPA and WPA2 standards and is a system that protects the security of wireless computer networks (Wi-Fi). WPA encryption protocol is used to improve and replace WEP encryption protocol. There are currently four authentication methods for WPA (Wi-Fi Protected Access) encryption: WPA, WPA-PSK, WPA2, and WPA2-PSK. There are two types of encryption algorithms used: Advanced Encryption Standard (AES) and Temporal Key Integrity Protocol (TKIP). Note that WPA-PSK can only use TKIP encryption. WPA2 (WPA Second Edition) WPA2 is an enhanced version of WPA. Compared with WPA, WPA2 has added encryption that supports AES. Moreover, WPA2 can be encrypted using AES+TKIP. However, now WPA or WPA2 is no longer safe and reliable. How to prevent? First , do not connect outdoor Wi-Fi, such as public places, even if it seems to be well-known Wi-Fi, do not connect, Xiaobian tried a special firmware system router, WeChat account, etc. can be captured, no In any safe place, people with malicious intentions even set names consistent with the famous Wi-Fi to deceive everyone. In fact, this is no matter what kind of method Wi-Fi uses to encrypt. It should be said that everyone should try to avoid connecting to outdoor Wi-Fi services. In particular, some routing systems have been modified, such as prompting login with WeChat, QQ, etc. to use the network. Be more careful. Second , APPs that share Wi-Fi passwords should not be used. The problem is not sharing APPs, but rather the shared wireless, unknown and secure wireless signals are directly connected, and you do not know what will happen. Third , the routing of your home can hide wireless SSID broadcasts, the simplest and straightforward. This makes it impossible for someone else to search for your wireless name. If you encounter a special device (such as a smart socket) that needs to broadcast an SSID before it can be connected, select the whitelist mode to bind the MAC address and register it with your home device. In fact, the security of wireless signals has always been a concern, which is also why the early WEP encryption protocol was so quickly eliminated. In addition, Xiao Bian also recommended the use of two different combinations of cross-characters, such as A1B2C3, while replacing 123 and pressing Shift after the input! Characters such as @#, which can also make brute-force life unrequited, to maximize protection of their own network security. Reverse Conducting Thyristor(RCT)
Reverse Conducting Thyristor(RCT) is also called Reverse- appreciation Thyristor.The characteristic is that a diode is connected in reverse parallel between the anode and cathode of thyristor, so that the transmitting junction of anode and cathode is short-circuited.As a result of this special circuit structure, it has high voltage resistance, high temperature resistance, short turn-off time, low switching voltage and other good performance.For example, the turn-off time of the reverse thyristor is only a few microseconds, and the working frequency is dozens of KHZ, which is better than the fast thyristor (FSCR).This device is suitable for switching power supply and UPS uninterrupted power supply. One RCT can replace one thyristor and one continuous current diode respectively.
Reverse Conducting Thyristor,Original Reverse Conducting Thyristor,New Reverse Conducting Thyristor,Reverse-Conducting Thyristor 2200V YANGZHOU POSITIONING TECH CO., LTD. , https://www.cnpositioning.com